Explain How a Message Is Encrypted End-to-end Work
How Does iMessage Encryption Work. Often a long message is encrypted using a much faster symmetrical method which uses the same key for locking and unlocking the message.
/cdn.vox-cdn.com/uploads/chorus_asset/file/22230709/GettyImages_1295784980.jpg)
Is The Signal App Safe The Encrypted Messaging Platform And Whatsapp Alternative Explained Vox
However if you use iCloud Backup to back up anything on your device it seems that iCloud gets a copy of the key that can decrypt the messageseven if youre not backing up messages using iCloud.

. Currently it is the safest way of data transferring over internet. Some send a message encrypted by an Ephemeral key and encrypt only. It uses a complex algorithm called a cipher that makes the message sent unreadable.
The solution is to use the public key method to send only the shared key. The content of your messages and calls in an end-to-end encrypted conversation is protected from the moment it leaves. Answer 1 of 2.
The utilized AES-key is then encrypted with the public key of the receiver. Only the genuine recipient has another key to unscramble and access it. Bob wants to send Alice a message.
The end-to-end encrypted system provides each with a public-private key pair whereby their public keys are stored on the server and their private keys are stored on their device. End-to-End encryption does work best in protecting free speech while shielding dissidents activists and journalists from instances of intimidation and law enforcement or third party agencies peaking into your private data and decrypts messages sent. E2EE uses encryption to protect your messages all the way from their origin you to their destination the person youre talking to.
Unlocking as a recipient is done automatically. How does end-to-end encryption work. This is called end to end encryption.
Only authorized parties can read or access that data. How end-to-end encryption works. Also read- Meaning of reset encrypted data on IPHONE Advantages of E2EE End to end encryption.
With E2EE data is encrypted on the senders system or device and only the recipient can decrypt it. Some services send individual encrypted messages to every participant I guess that was what Wire did but it may have been changed since. Apple has two services that host your messages.
This method also known as asymmetric cryptography encrypts and decrypts the message using distinct cryptographic keys. With end-to-end encryption it is users who issue codes that can only be decrypted by the other persons device. No one else on the way who does not have the key can access it.
Most explanations of E2EE feature two classic characters Alice and Bob. The message or file is usually made illegible on the device of the sender by applying hybrid encryption. Another advantage follows from end-to-end encrypted messages being undecryptable by anyone other than the recipient.
End-to-end encryption adds extra security and protection to your messages and calls in a conversation so that only you and whoever youre talking to can see hear or read them. No one can change the message. This open-source enterprise collaboration tool provides end-to-end encryption for your messages along with unlimited audio and video.
DOCUMENTS Document Sharing Made Easy. The scenario is this. Modern encryption methods work in such a way that if someone changes the encrypted data the message becomes garbled on decryption making the problem instantly clear.
End-to-end encryption is a method of encoding data messages or files. With E2EE the sender or creator encrypts the data and only the intended receiver or reader can decrypt it. For example if we are talking on WhatsApp with a person and that chat is end-to-end encrypted the user who sends a message is in turn issuing a code that can only be decrypted by the other person.
What makes end-to-end encryption unique compared to other encryption systems is that only the endpoints -- the sender and the receiver -- are capable of decrypting and reading the message. Once received the message can be decrypted using a key provided by the sender of the message. Symmetric key encryption which is also known as single-key or secret key encryption also provides an unbroken layer of encryption from sender to recipient but it uses only one key to.
For years the messaging service was also privy to the conversations we were having and this data was then used to spam us with ads that were tailored to each user based on their topics of interest their. It allows users to bring their WhatsApp Signal and Telegram chats into its personal messaging variant the Element One. When end-to-end encrypted your messages and calls are secured so only you and the person youre communicating with can read or listen to them and nobody in between not even WhatsApp.
Alice wants to send Bob an encrypted message. You can be the owner of your data which means you can store your messages at your end. There is no one method.
Messages in iCloud syncs your messages between devices and it is end-to-end encrypted. Only users who possess a secret key can decipher or decrypt the message into plaintext. Thats why it is called an end to end encryption because the message gets encrypted when it is sent and only gets decrypted at the end of it.
Send PDFs documents spreadsheets slideshows and more without the hassle of email or file-sharing apps. When you send a message using Viber your messages are encrypted locked while they are in transit and then decrypted unlocked when they reach the intended recipient. It prevents third parties from accessing data while it is being transferred from one end system or device to another.
End-to-end encryption begins with cryptography a method for protecting information by transforming it into an unreadable format called ciphertext. This is very secure except that the key needs to be shared with the recipient. Each Viber account has a unique key.
Public keys are widely distributed and are used to encrypt or lock messages. For encryption to take place the sending user who has an encryption key can encode or scramble the data and then send it. The generation of a public-private key pair ensures the security of end-to-end encryption.
She uses Bobs public key to encrypt her message to him. Learn more about how this works on our whitepaper. When you see the term End-To-End encryption it generally means that when you send a message to a contact the message is only visible to the two of you.
How does end-to-end encryption work. End-to-end encryption E2EE is a method of enabling secure communications. Hybrid encryption is used for reasons of efficiency and implies that the message is encrypted with a symmetrical key eg.
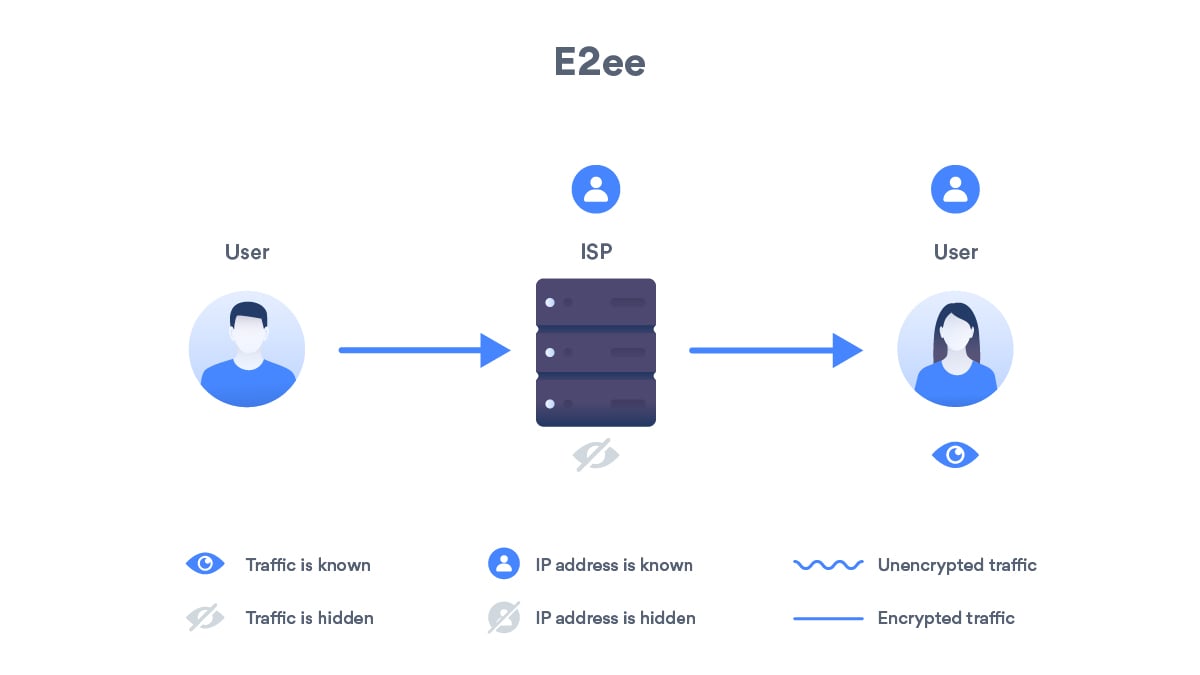
End To End Encryption Explained Nordvpn
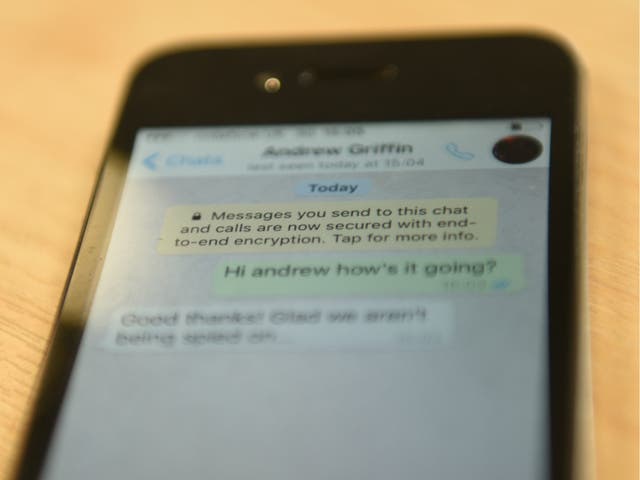
Whatsapp End To End Encryption Update Might Have Made Chat App Illegal In India The Independent The Independent

What Is End To End Encryption And What Are Its Pros And Cons Kaspersky Official Blog
Facebook Says Encrypting Messenger By Default Will Take Years Wired

Explained Whatapp Calls End To End Encrypted But What Does It Mean For You Technology News
Whatsapp Signal And End To End Encryption By Firat Civaner Medium

End To End Encryption How Do Alice And Bob Exchange Keys In A Secure Manner How Does Alice K End To End Encryption Cyber Security Network Security Technology
Facebook Messenger Adds End To End Encryption In A Bid To Become Your Primary Messaging App Techcrunch

End To End Encryption E2ee Explained Engineering Education Enged Program Section
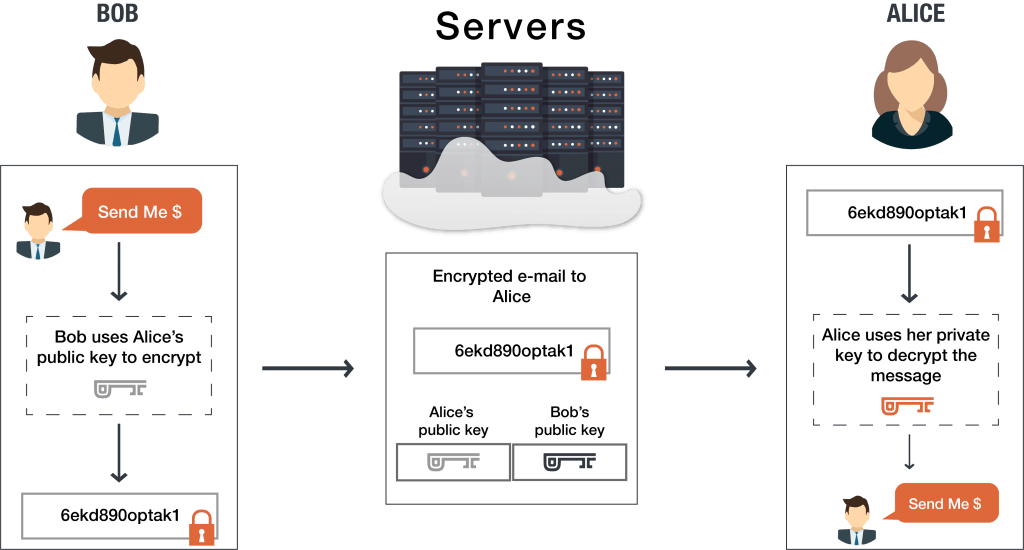
End To End Encryption And Guide On How It Works Preveil
Whatsapp End To End Encryption How It Works And What It Means For Users Technology News The Indian Express
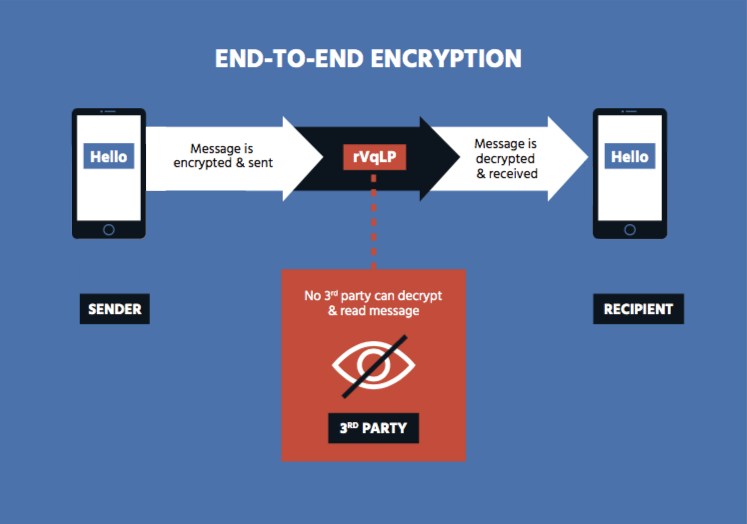
Encryption Brief Internet Society
Explain Like I M 5 End To End Encryption By Cossack Labs Medium

Are Your Whatsapp Chats Secure Here S What End To End Encryption Means Technology News The Indian Express

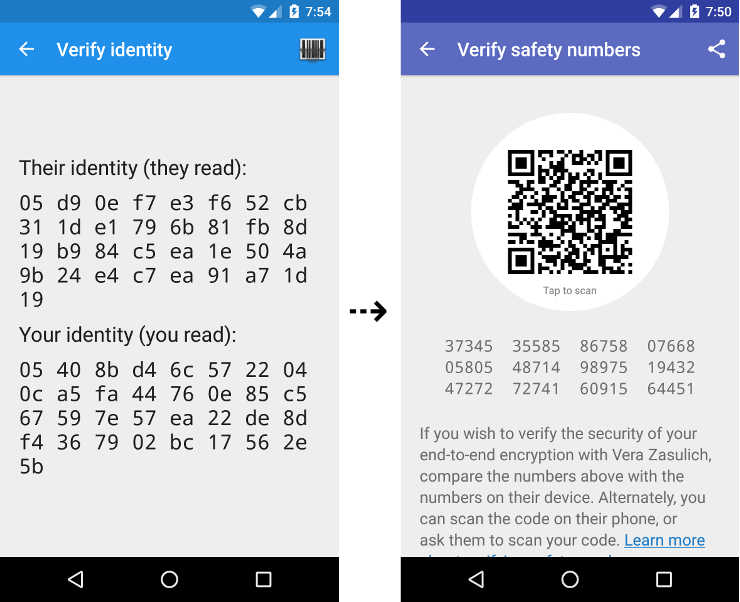
How To Verify That Whatsapp Messages Are Encrypted Up Running Technologies Tech How To S
End To End Encryption Explained Nordvpn
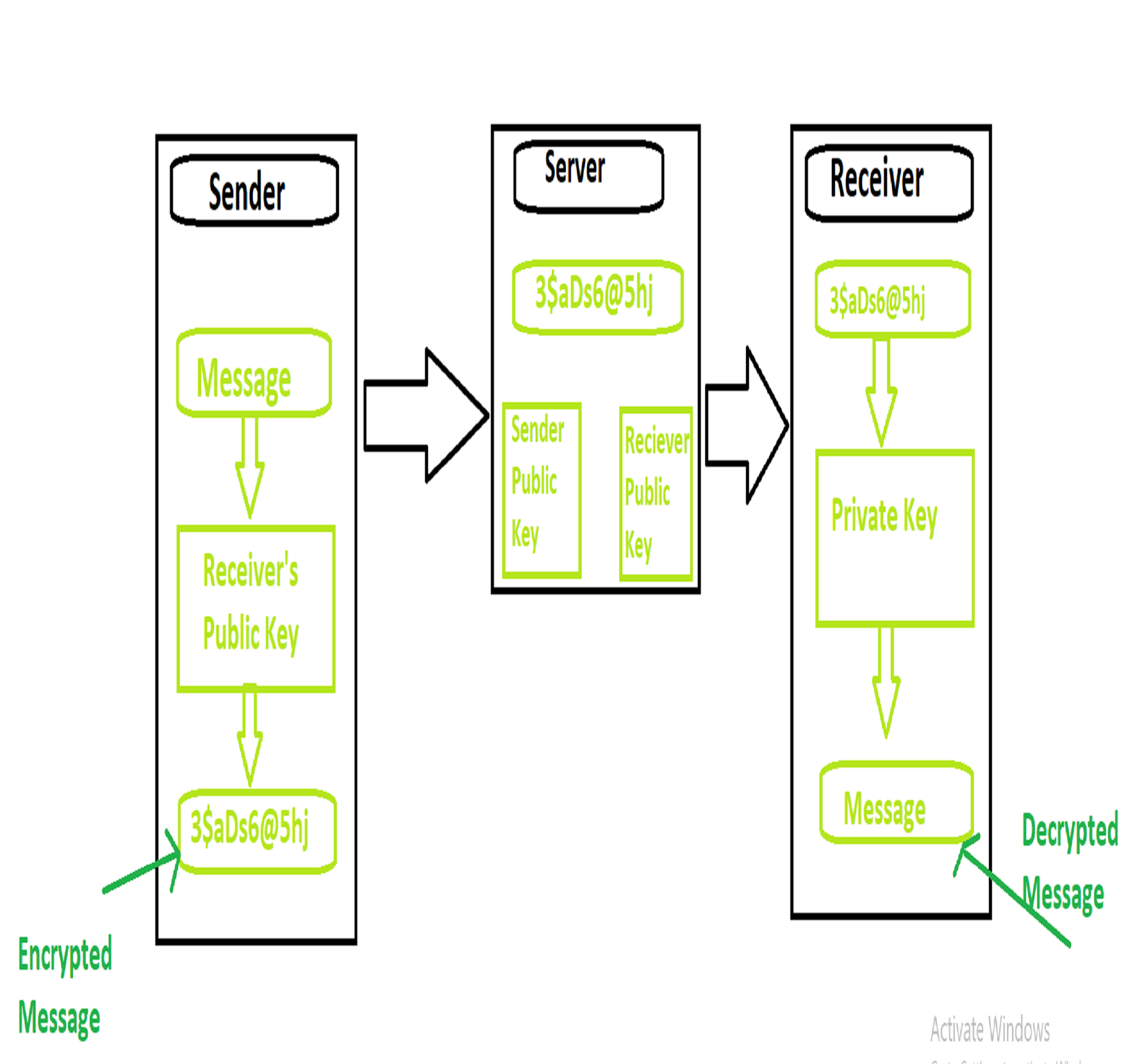
What Is E2ee End To End Encryption Geeksforgeeks

End To End Encrypted Chat In Flutter

Weakened Encryption The Threat To America S National Security Third Way
Comments
Post a Comment